- From: <rjc@enterprivacy.com>
- Date: Sun, 24 Mar 2019 21:18:35 -0700
- To: "Harshvardhan J. Pandit" <me@harshp.com>, public-dpvcg@w3.org
- Message-Id: <cd2e7d01790a609094bfe0a3b05ce7affb9b3074@webmail.dreamhost.com>
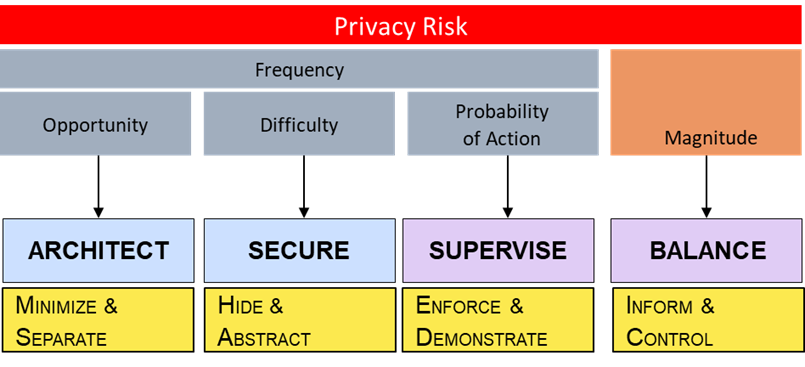
Harsh, the two strategies I identified are security related. Below the strategies are tactics and below the tactics would be techniques, which is what you've described. HIDE Strategy (4 Tactics) * Obfuscate * Mix * Restrict * Dissociate ABSTRACT Strategy (3 Tactics) * Summarize * Group * Perturb You mentioned four techniques: ENCRYPTION - falls under the Obfuscate tactic as it's used to reduce the understandability of information ACCESS CONTROL - falls under the Restrict tactic as it's used to restrict access to information SEPARATION and SECURE deletion I put under the Architecture strategies of SEPARATE and MINIMIZE, respectively. While both techniques reduce risk they do so, not through securing the data but reducing the opportunity for threat actors. SEPARATE makes it more time consuming because a threat actor must repeat their effort multiple times. Minimizing information (like through secure deletion) doesn't "secure" the information because once you delete it, there is nothing to "secure." Similar to separating information, in reduces opportunity for a threat actor. Here the reduction is temporal, because the threat actor has to act before the deletion occurs. For completeness, here are the two Architect strategies and tactics SEPARATE (2 tactics) * Distribute * Isolate MINIMIZE (4 tactics) * Exclude * Select * Strip * Destroy As with the two Secure strategies and underlying tactics there are hundreds of specific techniques that can be used to accomplish these strategies. I, nor anyone else that I'm aware, has attempted to catalog all of the techniques. I'm attaching below, a mapping of privacy risk factors to control strategies. While you could any technique under Architect and Secure as "security" controls, I think its import to distinguish how they reduce privacy risk, because that helps drive the decision of which controls to employ. Jason P.S. the efficacy of a particular control is also separate from the control itself and I would suggest making sure any techniques you adopt in a taxonomy ensure you're not mixing the concepts. For instance, you mentioned "secure deletion". I would suggest the control is deletion, but that's distinct from how good it is (i.e. overwriting with zeros, random data, multiple times, etc.) A similar argument could be made about all the others. To meet encryption, you could use ROT13 and that might be fine if your threat actor is a 7 year old kid but probably not against anyone else. ..................................................................... R. Jason Cronk | Juris Doctor Privacy and Trust Consultant | IAPP Fellow of Information Privacy ENTERPRIVACY CONSULTING GROUP [1] | CIPT, CIPM, CIPP/US, PbD Ambassador Privacy notices made simple: https://simpleprivacynotice.com [2] .................................................................... UPCOMING TRAINING Privacy by Design Professional: Cyprus (April [3]), Belarus - English/Russian (July) Online (coming soon): https://privacybydesign.training [4] ----- Original Message ----- From: "Harshvardhan J. Pandit" <me@harshp.com> To: public-dpvcg@w3.org Cc: rjc@enterprivacy.com Sent: Sun, 24 Mar 2019 18:06:34 +0000 Subject: Re: ISSUE-11: Taxonomies on storrage locations and restrictions as well as security measues and restrictions still undefined. Thanks Jason, it is a wonderful report for PbD-based approaches. I'm not sure how this fits in to the security requirements and restrictions taxonomy, which I see as being about data security techniques such as encryption, access control, separation, secure deletion, etc. Maybe this is relevant to have a separate taxonomy for Privacy by design? On 23/03/2019 18:01, rjc@enterprivacy.com wrote: > Sorry I haven't been very active. > > You might consider looking at the Data Oriented Strategies and Tactics > from Jaap-Henk Hoepman > > https://www.cs.ru.nl/~jhh/publications/pds-booklet.pdf > > These are the ones I use and it's been picked up by a number of data > protection authorities. I group his Hide and Abstract Strategies under > the heading of *Security*, where as Minimize and Separate are under a > heading of Architecture. > > Jason > > .*.*.*.*................................................................. > R. Jason Cronk | Juris Doctor > Privacy and Trust Consultant | IAPP Fellow of Information Privacy > *Enterprivacy Consulting Group <http://www.enterprivacy.com/>* | CIPT, CIPM, CIPP/US, PbD Ambassador > /Privacy notices made simple: https://simpleprivacynotice.com > <https://simpleprivacynotice.com/> > /.................................................................... > > *Upcoming Training** > *Privacy by Design Professional:Cyprus (April <https://enterprivacy.com/cyprus-training/>), Belarus - > English/Russian (July) > Online (coming soon):https://privacybydesign.training <https://privacybydesign.training/> > > > > ----- Original Message ----- > From: > "Harshvardhan J. Pandit" <me@harshp.com> > > To: > <public-dpvcg@w3.org> > Cc: > > Sent: > Fri, 22 Mar 2019 14:51:45 +0000 > Subject: > Re: ISSUE-11: Taxonomies on storrage locations and restrictions as > well as security measues and restrictions still undefined. > > > Hello, I tried looking up the relevant ISO standards for security > and to identify terms for a taxonomy. But I ran into two major problems: > > a) ISO holds a copyright on their specific codes and terms > > b) ISO standards are not open, so I cannot look at them in depth > > Maybe someone who does have access can check the relevant standards > and see how we can formulate the taxonomies. > > In light of this, I feel we need to re-evaluate what a taxonomy of > security (related to data) should contain. > > > Attached is a mapping between different security standards and > top-level criteria, which is very informational. > > And I'm sharing my notes for the security ISO standards: > > > ISO standards > > * mapping between GDPR and ISO27000 > http://www.iso27001security.com/ISO27k_GDPR_mapping_release_1.pdf > * There are two standards - ISO27001/2 and ISO27018 for cloud > based services > > > ISO27018 > > ISO27018 adds the following over ISO27001/2 (source random article > on the internet > https://advisera.com/27001academy/blog/2015/11/16/iso-27001-vs-iso-27018-standard-for-protecting-privacy-in-the-cloud) > > * Rights of the customer to access and delete the data > * Processing the data only for the purpose for which the customer > has provided this data > * Not using the data for marketing and advertising > * Deletion of temporary files > * Notification to the customer in case of a request for data > disclosure > * Recording all the disclosures of personal data > * Disclosing the information about all the sub-contractors used > for processing the personal data > * Notification to the customer in case of a data breach > * Document management for cloud policies and procedures > * Policy for return, transfer and disposal of personal data > * Confidentiality agreements for individuals who can access > personal data > * Restriction of printing the personal data > * Procedure for data restoration > * Authorization for taking the physical media off-site > * Restriction of usage of media that does not have encryption > capability > * Encrypting data that is transmitted over public networks > * Destruction of printed media with personal data > * Usage of unique IDs for cloud customers > * Records of user access to the cloud > * Disabling the usage of expired user IDs > * Specifying the minimum security controls in contracts with > customers and subcontractors > * Deletion of data in storage assigned to other customers > * Disclosing to the cloud customer in which countries will the > data be stored > * Ensuring the data reaches the destination > > https://en.wikipedia.org/wiki/Security_controls > ISO 27001 Controls and Objectives > https://en.wikipedia.org/wiki/ISO/IEC_27001 > http://www.foo.be/docs/iso/AnnexIX1302-ListOfControls-ISO-27001.pdf > ISO 27002 Security Control Objectives > http://praxiom.com/iso-17799-objectives.htm > http://praxiom.com/iso-27002-objectives.htm > > ISO/IEC 15408 Evaluation criteria for IT security > ISO/IEC 18045 Methodology for IT security evaluation > ISO/IEC 19608 Guidance for developing security and privacy > functional requirements based on > ISO/IEC 15408 > > ISO/IEC 27002 Code of practice for information security controls > ISO/IEC 17030 Guidelines for security and privacy in Internet of > Things (IoT) > ISO/IEC 27017 Code of practice for information security controls > based on ISO/IEC 27002 for > cloud services > > ISO/IEC 18033 Encryption algorithms > ISO/IEC 18370 Blind digital signatures > ISO/IEC 20008 Anonymous digital signatures > ISO/IEC 20009 Anonymous entity authentication > ISO/IEC 29191 Partially anonymous partially unlinkable authentication > ISO/IEC 20889 Privacy enhancing data de-identification techniques > ISO/IEC 27551 Attribute based unlinkable entity authentication > > JWG8 has proposed to recognize ISO/IEC 29134 (privacy impact assessment > Methodology) as a European standard (EN) > > ETSI > DTR/CYBER-0010, TR 103 370, Practical introductory guide to privacy > DTS/CYBER-0013, TS 103 485, Mechanisms for privacy assurance and > verification > DTS/CYBER-0014, TS 103 486, Identity management and naming schema > protection mechanisms > DTS/CYBER-0020, TS 103 458, Application of Attribute Based > Encryption (ABE) for data protection > on smart devices, cloud and mobile services > > Regards, > > Harsh > > On 12/02/2019 13:56, Data Privacy Vocabularies and Controls > Community Group Issue Tracker wrote: > > ISSUE-11: Taxonomies on storrage locations and restrictions as well as security measues and restrictions still undefined. > > https://www.w3.org/community/dpvcg/track/issues/11 > > > > > Raised by: > > > > On product: > > > > > > -- > > > > --- > > > > Harshvardhan Pandit > > > > PhD Researcher > > > > ADAPT Centre > > > > Trinity College Dublin > -- --- Harshvardhan Pandit PhD Researcher ADAPT Centre Trinity College Dublin Links: ------ [1] http://webmail.dreamhost.com/HTTP://WWW.ENTERPRIVACY.COM/ [2] https://simpleprivacynotice.com/ [3] https://enterprivacy.com/cyprus-training/ [4] https://privacybydesign.training/
Attachments
- image/png attachment: image.png
Received on Monday, 25 March 2019 04:19:08 UTC