- From: Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net>
- Date: Sun, 5 Feb 2023 06:58:42 +0000
- To: Anders Rundgren <anders.rundgren.net@gmail.com>, Wayne Chang <wayne@spruceid.com>
- CC: Christopher Allen <ChristopherA@lifewithalacrity.com>, "G. Ken Holman (g.ken.holman@gmail.com)" <g.ken.holman@gmail.com>, Steve Capell <steve.capell@gmail.com>, "public-credentials (public-credentials@w3.org)" <public-credentials@w3.org>, "sam@prosapien.com" <sam@prosapien.com>
- Message-ID: <MWHPR1301MB2094E1E9686BEA4F18FD16E5C3D59@MWHPR1301MB2094.namprd13.prod.outlook.>
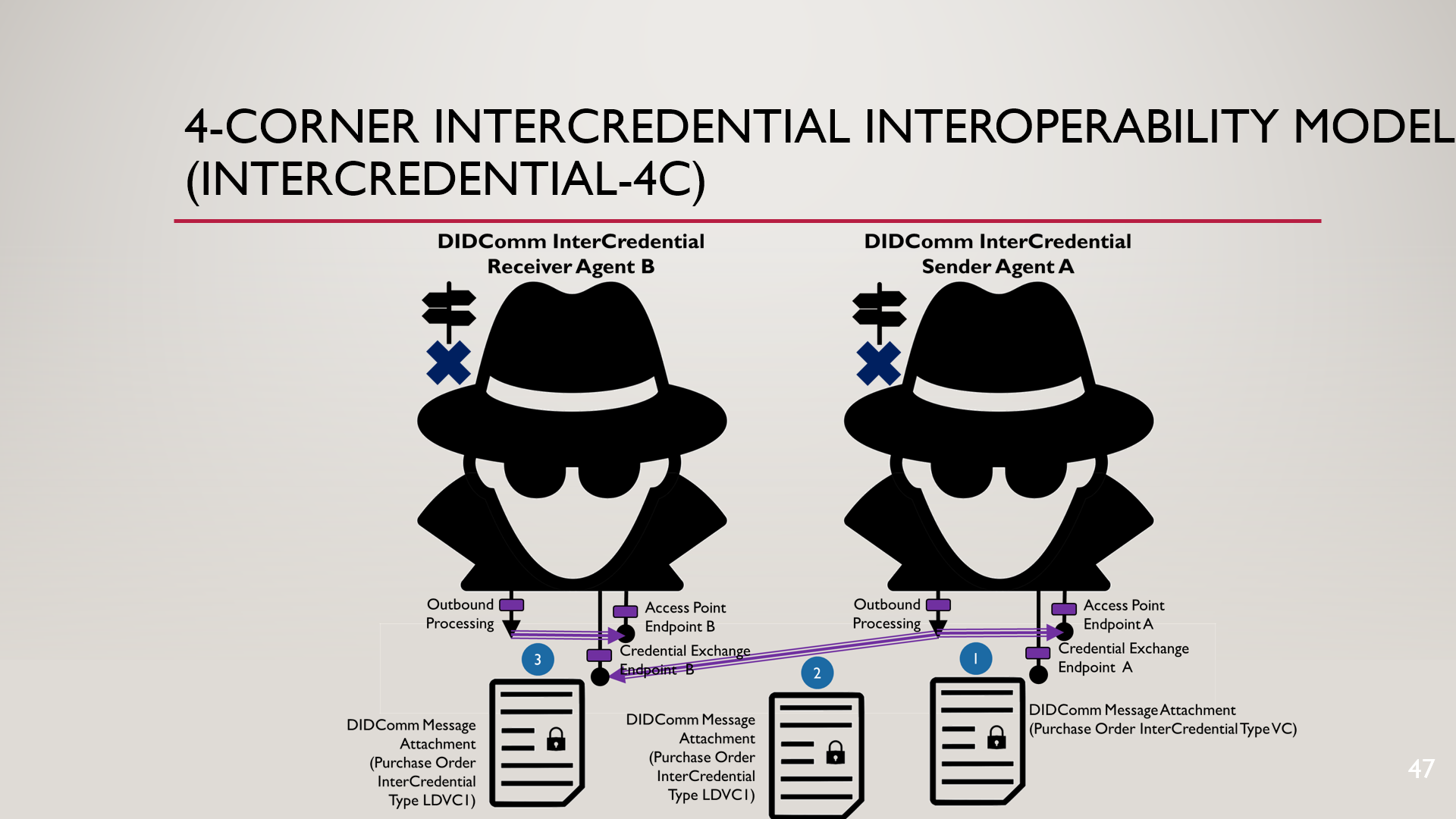
RE: Since I agree with what Steve Capell wrote about message integrity etc., I'm curious about how the revised solution copes with this. In these scenarios, the InterCredential Sender is also the (self) Issuer of the purchase order verifiable credential, so there is no loss of message integrity for the Sender to decide (for a particular InterCredential Receiver relationship), to decide to use its Access Point endpoint to transform and resign the InterCredential (1) before sending it to the InterCredential Receiver’s Credential Exchange endpoint (2). [cid:image001.png@01D938FC.FC0DFEF0] -----Original Message----- From: Anders Rundgren <anders.rundgren.net@gmail.com> Sent: Saturday, February 4, 2023 11:12 PM To: Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net>; Wayne Chang <wayne@spruceid.com> Cc: Christopher Allen <ChristopherA@lifewithalacrity.com>; G. Ken Holman (g.ken.holman@gmail.com) <g.ken.holman@gmail.com>; Steve Capell <steve.capell@gmail.com>; public-credentials (public-credentials@w3.org) <public-credentials@w3.org>; sam@prosapien.com Subject: 4-Corner Credential Interoperability Model On 2023-02-05 5:31, Michael Herman (Trusted Digital Web) wrote: > 80% of it. I’ll have a full demo at IIW. There’s actually a small flaw in the “version 0.65” diagram in my previous post because it is difficult to actually transform and re-sign the credential on the right side as well as re-auth-encrypt the DIDComm credential exchange message with the re-signed credential. “Necessity being the mother of invention” led to the creation of the concept of DIDComm Agent logical composition: If you have N DIDComm Agents connected serially from a message transfer perspective, this scenario can be recoded as a single physical DIDComm Agent with N inbound service endpoints. Using DIDComm Agent logical composition, the equivalent working version 0.66 solution looks like this Since I agree with what Steve Capell wrote about message integrity etc., I'm curious about how the revised solution copes with this. AFAICT, end-2-end security requires the communicating parties agreeing on everything from formats to cryptographic algorithms and trust anchors. This only works satisfactory for closed-loop systems which is why I began toying with public discovery services. I have had this running (albeit only in lab-scale...) since 2015. https://www.linkedin.com/posts/andersrundgren_many-payment-authorization-systems-build-activity-7002012686137835520-p-2X Since discovery service information can be cached, the overhead is quite limited. Yes, cache refreshes of course add some minor delays every now and then. IMNSHO, the ISO 20022 folks are on the wrong track; extremely complex messages (with tons of "nice to have" options subject to interpretation), is primarily an asset for consultants :) Anders > > *From:* Wayne Chang wayne@spruceid.com<mailto:wayne@spruceid.com> <mailto:wayne@spruceid.com> > *Sent:* Saturday, February 4, 2023 10:08 PM > *To:* Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net<mailto:mwherman@parallelspace.net>> > *Cc:* Christopher Allen <ChristopherA@lifewithalacrity.com<mailto:ChristopherA@lifewithalacrity.com>>; G. Ken Holman (g.ken.holman@gmail.com<mailto:g.ken.holman@gmail.com>) <g.ken.holman@gmail.com<mailto:g.ken.holman@gmail.com>>; Steve Capell <steve.capell@gmail.com<mailto:steve.capell@gmail.com>>; public-credentials (public-credentials@w3.org<mailto:public-credentials@w3.org>) <public-credentials@w3.org<mailto:public-credentials@w3.org>>; sam@prosapien.com<mailto:sam@prosapien.com> > *Subject:* Re: 4-Corner Credential Interoperability Model > > Cool, do you have any code to run this? > > On Sat, Feb 4, 2023 at 19:38 Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net <mailto:mwherman@parallelspace.net<mailto:mwherman@parallelspace.net%20%3cmailto:mwherman@parallelspace.net>>> wrote: > > If you use some DIDComm imagination, it's easy to see how the 4-Corner Credential Interoperability Model is highly complementary to supporting a layered VC model ...here's a glimpse. "More news at 11..." > > -----Original Message----- > From: Steve Capell <steve.capell@gmail.com <mailto:steve.capell@gmail.com<mailto:steve.capell@gmail.com%20%3cmailto:steve.capell@gmail.com>>> > Sent: Saturday, February 4, 2023 4:24 PM > To: Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net <mailto:mwherman@parallelspace.net<mailto:mwherman@parallelspace.net%20%3cmailto:mwherman@parallelspace.net>>> > Cc: public-credentials (public-credentials@w3.org<mailto:public-credentials@w3.org> <mailto:public-credentials@w3.org>) <public-credentials@w3.org <mailto:public-credentials@w3.org<mailto:public-credentials@w3.org%20%3cmailto:public-credentials@w3.org>>>; G. Ken Holman (g.ken.holman@gmail.com<mailto:g.ken.holman@gmail.com> <mailto:g.ken.holman@gmail.com>) <g.ken.holman@gmail.com <mailto:g.ken.holman@gmail.com<mailto:g.ken.holman@gmail.com%20%3cmailto:g.ken.holman@gmail.com>>>; Christopher Allen <ChristopherA@lifewithalacrity.com <mailto:ChristopherA@lifewithalacrity.com<mailto:ChristopherA@lifewithalacrity.com%20%3cmailto:ChristopherA@lifewithalacrity.com>>>; sam@prosapien.com<mailto:sam@prosapien.com> <mailto:sam@prosapien.com> > Subject: Re: 4-Corner Credential Interoperability Model > > I think the 4-corner model is the opposite of the VC model. It’s a EDI message routing framework that delegates the problem of trust (ie trader identity verification) to EDI hubs. Hubs perform a “service” to their authenticated subscribers to map messages to the format they need - so forget about document integrity (how do you maintain a signature when the document is transformed at two hubs?). There’s nothing verifiable about the message that eventually lands with the receiver (through 2 hubs). Instead the parties have to trust that the hubs have properly identified their clients and have not lost anything in translation > > It’s also expensive (every message attracts two clip-fees). I’ve never seen this model achieve any significant uptake except in cases where it is mandated by a national regulator > > Kind regards > > Steven Capell > > Mob: 0410 437854 > > > On 4 Feb 2023, at 10:49 pm, Michael Herman (Trusted Digital Web) <mwherman@parallelspace.net <mailto:mwherman@parallelspace.net<mailto:mwherman@parallelspace.net%20%3cmailto:mwherman@parallelspace.net>>> wrote: > > > > > > A colleague of mine, Ken Holman from Ottawa, recently produced a conference paper on the topic of the 4-Corner Credential Interoperability Model. It's originated in the OASIS Universal Business Language (OASIS-UBL) community where they were experiencing problems with spec compliance, interoperability, and low/slow technology adoption rates. UBL is a set of 90+ schemas defined for the most commonly used business documents used in commerce today. > > > > > > The 4-Corner Credential Interoperability Model is a simple, efficient, low-cost approach to enable different communities or trading associations to easily interoperate through the exchange of different types of credentials. For example, this would be a stepping stone for enabling a layered approach to how verifiable credentials are defined, used, and exchanged - an opportunity to move away from a "one-size fits all" niche VCDM specification to a layered model that addresses the dual needs of: > > > a) the layering of simple, more generic models through to more complex > > > niche credential specifications, as well as > > > b) an interoperability model that is simple, secure, efficient, and low-cost. > > > > > > Live Presentation: Case study of a semantic library underpinning the > > > 4-corner model for document exchange 2022-11-08 > > > > > > https://www.linkedin.com/posts/gkholman_ken-holman-case-study-of-a-sem <https://www.linkedin.com/posts/gkholman_ken-holman-case-study-of-a-sem> > > > antic-library-activity-7001714323223977985-IKbA > > > > > > Case study of a semantic library underpinning the four-corner model > > > for document exchange > > > https://doi.org/10.1075/da.2022.holman.four-corner-model <https://doi.org/10.1075/da.2022.holman.four-corner-model> > > > Proceedings of Declarative Amsterdam 2022 (7 and 8 November 2022) > > > Available under the CC BY 4.0 license. > > > > > > > > > > > > Best regards, > > > > > > Michael Herman > > > > > > Web 7.0 > > > > > > > > > <winmail.dat> >
Attachments
- image/png attachment: image001.png
Received on Sunday, 5 February 2023 06:59:01 UTC