- From: Leonard Rosenthol <lrosenth@adobe.com>
- Date: Mon, 18 Jul 2022 17:10:38 +0000
- To: Stephen Curran <swcurran@cloudcompass.ca>, Kerri Lemoie <kerri@openworksgrp.com>
- CC: Manu Sporny <msporny@digitalbazaar.com>, W3C Credentials CG <public-credentials@w3.org>, "public-vc-edu@w3.org" <public-vc-edu@w3.org>
- Message-ID: <DM8PR02MB81819167409DADC01785BDFACD8C9@DM8PR02MB8181.namprd02.prod.outlook.com>
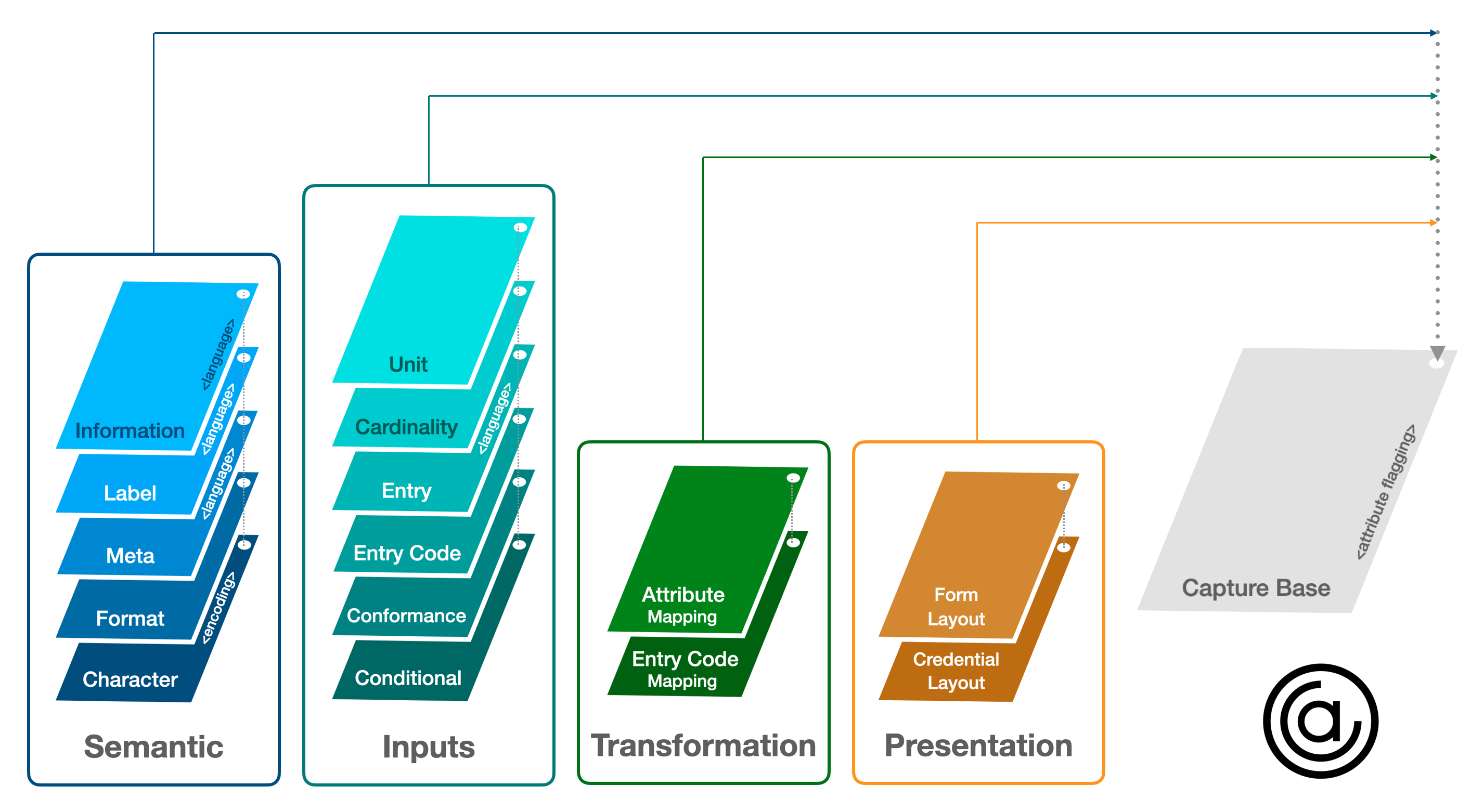
I’ll note that in C2PA, we have also been spending time on the related issue of “updatable UX information”, such as newer (or corrected) localizations. The biggest concern for us is in trying to tie that distribution of the material with the signature/credential/trust of the asset itself. Since the material in question is designed to be updated, it is not possible to store a hash of it ahead of time (aka at time of publication/distribution of the asset) and so how would the UX know that the retrieved material is indeed the material that the author/publisher of the asset approves? Since the signing certificate of the asset is not the same as domain certificates for sites – different EKUs – how can you be sure? Sorry I am not offering answers, but hope wanted to present another take on the problem. Leonard From: Stephen Curran <swcurran@cloudcompass.ca> Date: Monday, July 18, 2022 at 12:43 PM To: Kerri Lemoie <kerri@openworksgrp.com> Cc: Manu Sporny <msporny@digitalbazaar.com>, W3C Credentials CG <public-credentials@w3.org>, public-vc-edu@w3.org <public-vc-edu@w3.org> Subject: Re: Rendering Verifiable Credentials @ RWoT11 EXTERNAL: Use caution when clicking on links or opening attachments. Hi Manu -- sounds like we're all getting to the UX issue. Shows the progress being made in the community! In addition to the rendering for appearance, we're very much interested in multilingual presentation of credentials, including being able to provide informational data about the attributes. Ideally, this information is verifiably linked to a known (dare we say "trusted") party (e.g. the schema publisher or credential issuer), and used by holder software (e.g. a wallet) to render the credential, and perhaps also be verifiers for displaying attributes included in a presentation. In the Aries/AnonCreds world, we're applying the work being done in the "Overlay Capture Architecture"(1, 2) (OCA) open specification. OCA provides a mechanism for defining layers of information about any data model. Its roots are in Pharma industry interop, but applies very nicely to credentials, and is also being used in the Chained Credentials (ACDC) / KERI work. Basically, the publisher of the schema or the issuer of a credential (or other "trusted" party) defines an "OCA Bundle" -- a base layer consisting mainly of the names of the data attributes in the credential, and then a set of overlays, each of which adds a dimension of semantic information. We're using these layers: * Multilingual naming of the credential type and issuer (one layer per language) * Multilingual labels per attribute * Multilingual help information per attribute * Image and the layout of multilingual labels and data over the image * Multilingual Code/Value (e.g. enumerated code values like Vaccine names) * Flagging of data elements that are PII (enabling UX opportunities for holder software when creating presentations to send to verifiers) * Data format * Data encoding * Suppression of attributes in the credential but deliberately not populated by the issuer (e.g. nulls) From a practical perspective, all but the image/data layout can be provided in source form using a structured spreadsheet (with a tab per language) that is converted to the OCA Bundle (basically, a zip file of cryptographically linked JSON files -- one per overlay). The use of a spreadsheet simplifies the business process of collecting multilingual data elements. The OCA Bundle is then published by an appropriate participant. With AnonCreds, we're having the schema publisher or credential issuer publish a resolvable, signed instance of the OCA Bundle that the holder or verifier can retrieve on receiving a credential or presentation. Tooling is available for all the steps, and it's a relatively light lift to add the capability to Aries to provide required (multilingual!!!!) capabilities, and options to render beautiful credentials (multilingual labels/data over image). A link to enable resolving the OCA Bundle could be put into the credential itself as an attribute, although for AnonCreds, we're going to be use the related identifiers (the schema and the issuer credential type) as the link to finding trusted, signed OCA Bundles. I'm not likely not going to make it to RWoT in Den Hague, but would be glad to discuss this with anyone interested in this approach to the challenge. [cid:ii_l5qwvllt0] (1) Overlays Capture Architecture -- https://oca.colossi.network/<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Foca.colossi.network%2F&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=ucTGz2rVs5fWr%2BBzIKe2LQGVoN3R5FqiOqX4N%2B7fk0w%3D&reserved=0> (2) OCA Specification: https://oca.colossi.network/v1.0.0.html<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Foca.colossi.network%2Fv1.0.0.html&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=iwUOdgb10VDp8wqQ8fVbQj5XqR5g%2F7QI099ahzyaEJg%3D&reserved=0> On Mon, Jul 18, 2022 at 7:14 AM Kerri Lemoie <kerri@openworksgrp.com<mailto:kerri@openworksgrp.com>> wrote: Hi Manu, We have an open issue for this in vc-edu. I added the archive link to your email to this issue: https://github.com/w3c-ccg/vc-ed/issues/16<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fw3c-ccg%2Fvc-ed%2Fissues%2F16&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=fBVtKMbhjXKASrkkmnWObMiC%2BTfEDQoyEkV9TzRP79o%3D&reserved=0> I’m also CCing the vc-edu mailing list and will mention in today’s call. This is something the task force would like to stay in the loop on. I can’t offer direct assistance right now but can confirm that it has come up frequently with wallet providers and issuers of Open Badges. Thanks! K. On Jul 17, 2022, at 5:21 PM, Manu Sporny <msporny@digitalbazaar.com<mailto:msporny@digitalbazaar.com>> wrote: Hey W3C Credentials CG, VCWG, and APAWG (bcc'd), The Verifiable Credentials ecosystem is experiencing increasing adoption in a variety of markets such as education, supply chain, retail, banking and finance, workforce training, and corporate and government identification cards. Each of these markets have issued credentials for hundreds of years and have (justifiably) pre-conceived notions and preferences around what their credentials should look like. Similarly, it is important to understand that visually representing a Verifiable Credential in certain ways could accidentally exclude those with accessibility needs. We need to consider people with visual needs such as larger font sizes, or the need to use colors that are easily discernable (e.g., red-green color blindness). We also need to design for those that cannot see, how do they navigate digital wallets and use Verifiable Credentials? This draft Rebooting the Web of Trust 11 paper explores ways in which the Verifiable Credentials data model could be extended to support visual, audio, and physical renderings for Verifiable Credentials. https://github.com/WebOfTrustInfo/rwot11-the-hague/blob/master/advance-readings/rendering-verifiable-credentials.md<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2FWebOfTrustInfo%2Frwot11-the-hague%2Fblob%2Fmaster%2Fadvance-readings%2Frendering-verifiable-credentials.md&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=igSYbQj%2BeLBsPFHxns94xwcjQkdt5PWcW%2Bk80DVsoJU%3D&reserved=0> So, three things: 1. This is a reminder that RWoT11 Early Bird papers are due in two days (July 19th): https://www.eventbrite.com/e/rebooting-the-web-of-trust-xi-2022-the-hague-tickets-347605426187<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fwww.eventbrite.com%2Fe%2Frebooting-the-web-of-trust-xi-2022-the-hague-tickets-347605426187&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=l5cQBsYY8%2B0gXF4Sb%2BLcP0HBqzNzGnxn3M%2FpSDMUOBk%3D&reserved=0> 2. We desperately need help from the Accessibility community if we have any chance of getting this even remotely right. 3. Is anyone interested in collaborating on this paper, or providing other ways you've approached rendering Verifiable Credentials? Thoughts? -- manu -- Manu Sporny - https://www.linkedin.com/in/manusporny/<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fwww.linkedin.com%2Fin%2Fmanusporny%2F&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=TUnPPwmG7vg3jr7%2B85s4e64dmz%2F8dLUvSogtpyzLSSY%3D&reserved=0> Founder/CEO - Digital Bazaar, Inc. News: Digital Bazaar Announces New Case Studies (2021) https://www.digitalbazaar.com/<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fwww.digitalbazaar.com%2F&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=gYT7dJUSIFpGoqf%2Be0eOsPra%2FZJvZzhzP32EKtBBkjg%3D&reserved=0> -- Stephen Curran Principal, Cloud Compass Computing, Inc. (C3I) Chair - Sovrin Foundation (sovrin.org) Schedule a Meeting: https://calendly.com/swcurran<https://nam04.safelinks.protection.outlook.com/?url=https%3A%2F%2Fcalendly.com%2Fswcurran&data=05%7C01%7Clrosenth%40adobe.com%7Cc8df5aa768ce4b0ebe4508da68dc3a01%7Cfa7b1b5a7b34438794aed2c178decee1%7C0%7C0%7C637937594151960307%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=pxPJbvq1vM1V32UetCWKMsupdtw2nFWRBBSQon6zOrc%3D&reserved=0>
Attachments
- image/png attachment: image.png
Received on Monday, 18 July 2022 18:46:04 UTC