- From: Johnathan Nightingale <johnath@mozilla.com>
- Date: Thu, 21 Feb 2008 09:12:43 -0500
- To: Stephen Farrell <stephen.farrell@cs.tcd.ie>
- Cc: W3 Work Group <public-wsc-wg@w3.org>
- Message-Id: <3FB43D35-0104-4670-92FE-B7411E25DDDF@mozilla.com>
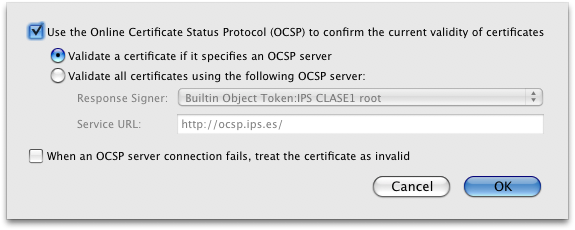
If it helps clarify at all, our behaviour in FF3 is to check OCSP responders if they are provided, but to assume "no response -> no revocation" unless a non-default option "When an OCSP server connection fails, treat the certificate as invalid" is chosen. This is less PKI-perfect than treating a lack of OCSP response as a hard fail, but that switch creates a fair bit of messy for the web as it currently is. I find this email a little odd, though, so I might be missing some context. IETF shouldn't need people to turn off OCSP checking in Firefox, given what I've said above. I guess maybe the thing that's conspiring to keep non-US connections from succeeding might just be timing out instead, in which case they could be seeing long load times as the connections time out, which could seem like failure. But that requires them to be using a very specific window of Firefox 3 betas, since we've dialed down the connection timeouts on OCSP for exactly this reason. :) Cheers, Johnathan PS - Here are the defaults we use in FF3: On 21-Feb-08, at 4:48 AM, Stephen Farrell wrote: > > FYI. Relevant to the proper handling of OCSP unavailable > error cases. > S. > > > From: Geoff Huston <gih@apnic.net> > Date: February 20, 2008 9:24:00 PM GMT-05:00 > To: Alexa Morris <amorris@amsl.com> > Cc: Iljitsch van Beijnum <iljitsch@muada.com>, IETF discussion list <ietf@ietf.org > >, James Galvin <galvin+ietf@elistx.com> > Subject: Re: amsl.com certificate? > > > The default setting in Firefox (and possibly safari) is to use OCSP > for > validation of certificates where OCSP is referenced. The *.ietf.org > certificate has as part of the Authority Information Field the value; > OCSP: URI: http://ocsp.starfieldtech.com > > This url is unreachable from many non-US sites, for reasons known only > to Godaddy I presume. > > The pragmatic workaround in firefox is to set the option to not using > OCSP for certificate validation. > > Geoff > > > > > > > > Alexa Morris wrote: >> As soon as the SSL problem was reported, AMS performed additional >> testing on >> many different computers. However, we were unable to duplicate this >> problem. >> If someone else experiences this issue and is concerned, please >> send an >> email ietf-action@ietf.org. Alternatively, please feel free to >> contact me >> directly at any time. >> >> Regards, >> Alexa >> >> >> ----------- >> Alexa Morris / Executive Director / IETF >> 48377 Fremont Blvd., Suite 117, Fremont, CA 94538 >> Phone: +1.510.492.4089 / Fax: +1.510.492.4001 >> Email: amorris@amsl.com >> >> Managed by Association Management Solutions (AMS) >> Forum Management, Meeting and Event Planning >> www.amsl.com <http://www.amsl.com/> >> >> >> On 2/20/08 10:45 AM, "James Galvin" <galvin+ietf@elistx.com> wrote: >> >>> AMS obtains certificates for their clients from Starfield >>> Technologies: >>> >>> <http://www.starfieldtech.com/> >>> >>> Do you have a concern about this choice or is your concern about >>> the fact that your browser didn't accept the certificate by default? >>> >>> If you have a concern about this choice it would help if you could >>> be specific about what that is. Their web site seems pretty >>> complete to me so any one of us could "check them out." I think we >>> need to trust AMS to make a good choice unless we can identify an >>> issue. >>> >>> As far your browser not accepting the certificate, I'm sure you >>> realize there a lot of reasons that could happen including the >>> latest version of Safari "missing" a particular root certificate. >>> >>> Jim >>> >>> >>> >>> >>> >>> -- On Wednesday, February 20, 2008 6:04 PM +0100 Iljitsch van >>> Beijnum <iljitsch@muada.com> wrote regarding amsl.com certificate? >>> -- >>> >>>> I just registered for IETF-71 and tried to pay. I wasn't bothered >>>> too much when I got an SSL warning for the former, but I >>>> hesitate to proceed with the latter, which is also under the >>>> amsl.com domain. >>>> >>>> My browser (the latest version of Safari on the Mac) complains >>>> that the issuer of the certificate is untrusted. That would be >>>> Starfield Secure Certification Authority. >>>> >>>> Is this a CA in good standing that we should trust? >>>> >>>> Iljitsch >>> _______________________________________________ >>> Ietf mailing list >>> Ietf@ietf.org >>> http://www.ietf.org/mailman/listinfo/ietf >>> >> >> >> _______________________________________________ >> IETF mailing list >> IETF@ietf.org >> http://www.ietf.org/mailman/listinfo/ietf >> > _______________________________________________ > IETF mailing list > IETF@ietf.org > http://www.ietf.org/mailman/listinfo/ietf > > > --- Johnathan Nightingale Human Shield johnath@mozilla.com
Attachments
- text/html attachment: stored
- image/png attachment: pastedGraphic.png
Received on Thursday, 21 February 2008 14:13:27 UTC