- From: Jed Rip via RT <sysreq@w3.org>
- Date: Wed, 04 Dec 2024 06:23:59 +0000
- CC: contact@w3.org, invoicing@w3.org, membership@w3.org, public-website-redesign@w3.org, team-liaisons@w3.org, w3t-pr@w3.org
- Message-ID: <rt-5.0.3+dfsg-3~deb12u2-3816733-1733293439-241.18068-18-0@w3.org>
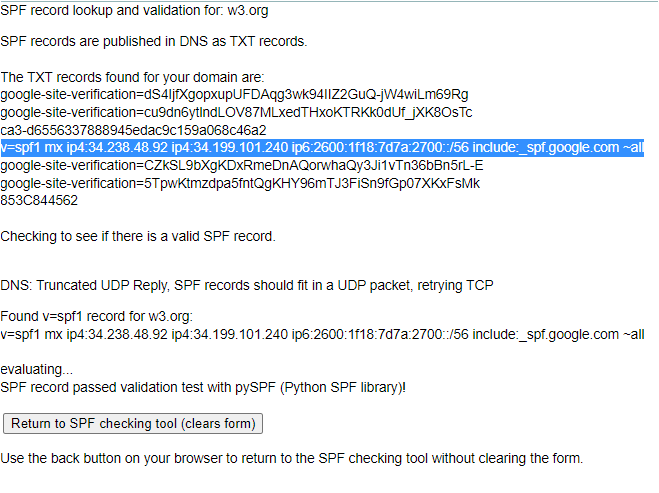
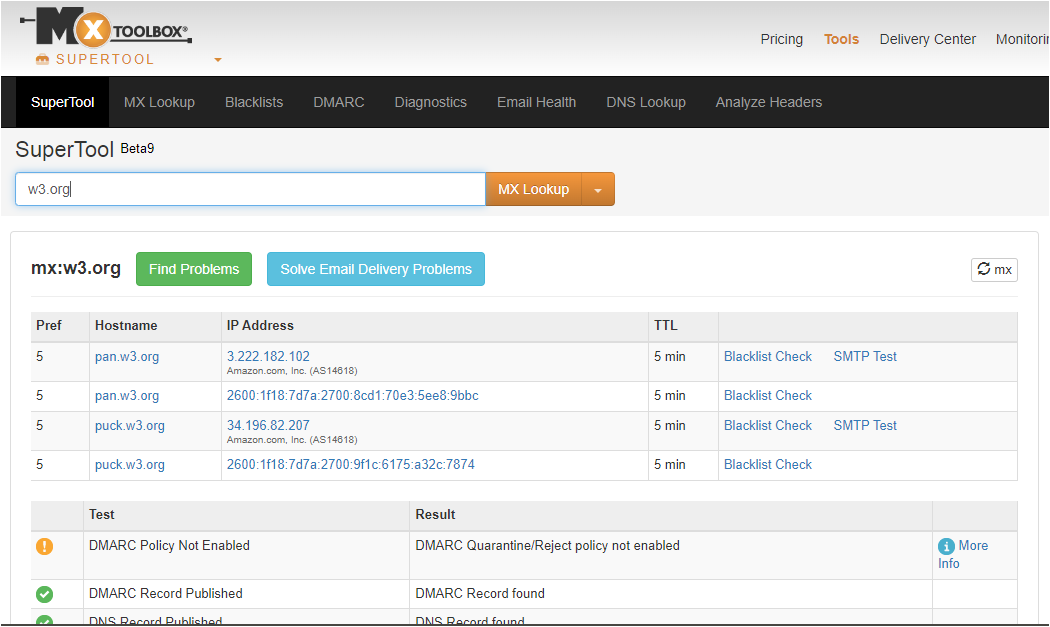
ping On Mon, Dec 2, 2024 at 8:49 PM Tzviya Siegman via RT <sysreq@w3.org> wrote: > Passing along this weird email. > > > > -------- Forwarded Message -------- > Subject: Re: Vulnerability Report: (Email Spoofing) > Resent-Date: Mon, 02 Dec 2024 08:14:03 +0000 > Resent-From: membership@w3.org > Date: Mon, 2 Dec 2024 13:11:36 +0500 > From: Jed Rip <jed.rip.protector@gmail.com> > To: membership@w3.org, invoicing@w3.org, w3t-pr@w3.org, > team-liaisons@w3.org, public-website-redesign@w3.org, sysreq@w3.org, > contact@w3.org > > > > Hello, > > How are you? > > I haven't received any update from you yet. > I am eagerly waiting for your reply. > Could you please confirm with me about the reported vulnerability and > its bounty reward? > > Looking forward to hearing from you soon. > > Thanks and Regards, > > On Sun, Oct 6, 2024 at 7:20 AM Jed Rip <jed.rip.protector@gmail.com> > wrote: > > Hello Team, > > > I am a security researcher and I provide information and knowledge > regarding “Vulnerability" on websites. I have found some > vulnerabilities on your website/domain. > > *DESCRIPTION:* > > * > *I just sent a forged email to my email addressthat appears to > originate from membership@w3.org <mailto:membership@w3.org>I was > able to do this because of the following: > > DMARC record lookup and validation forw3.org <http://w3.org> > > “No DMARC Record found” > And/ OR > "DMARC Quarantine/Reject policy not enabled" > > *Fix: > *1) Publish DMARC Record. (If not already Published) > 2)Enable DMARC Quarantine/Reject policy > 3)Your DMARC record should look like > "v=DMARC1; p=reject; sp=none; pct=100; ri=86400; > rua=mailto:info@domain.com <mailto:info@domain.com>" > > *And* > > As I have seen the SPF and TXT record for the w3.org > <http://w3.org> which is : > > > Found v=spf1 record for w3.org <http://w3.org>: > v=spf1 include:_spf.google.com <http://spf.google.com/> ~all > > > so valid record will look like : > > > Found v=spf1 record for w3.org <http://w3.org>: > > v=spf1 include:_spf.google.com <http://spf.google.com/> -all > > *What's the issue : > * > What’s the issue: as u can see in the article difference between > softfail and hardfail you should be using fail as Hardfail as it > doesn’t allow anyone to send spoofed emails from your domains, In > current SPF record you should replace (?) or > > (~) with (-) at last before all , - is strict which prevents all > spoofed emails except if you are sending > > You can validate by testing yourself over here: mxtoolbox.com > <http://mxtoolbox.com/> > > This is useful in phishing, and this type of vulnerability is > newsworthy > ( > http://bits.blogs.nytimes.com/2015/04/09/sendgrid-email-breach-was-used-to-attack-coinbase-a-bitcoin-exchange/ > < > http://bits.blogs.nytimes.com/2015/04/09/sendgrid-email-breach-was-used-to-attack-coinbase-a-bitcoin-exchange/ > > > > > https://medium.com/@hotbit/official-statement-notices-of-counterfeit-email-listing-hotbit-io-d1d240005d35 > < > https://medium.com/@hotbit/official-statement-notices-of-counterfeit-email-listing-hotbit-io-d1d240005d35 > > > > This can be done using any php mailer tool like this , > > <?php > $to = "VICTIM@example.com <mailto:VICTIM@example.com>"; > $subject = "Password Change"; > $txt = "Change your password by visiting here - [VIRUS LINK HERE]l"; > $headers = "From: membership@w3.org <mailto:membership@w3.org>"; > mail($to,$subject,$txt,$headers); > ?> > > *IMPACT:* > Due to this vulnerability, any hacker can send a forged email to > your customers using your domain .Thus, getting sensitive > information of your customers like login details, downloading a > virus/malware etc. > > Also When an attacker sends an email to your customers asking them > to change their password. The customer, after seeing the mail, might > consider the mail as legit and falls for the trap. > > In doing this the attacker can take them to his website where > certain JavaScript is executed which steals the customer's session > id and password. > > The results can be more dangerous and impactful. > > A study shows why DMARC and SPF are crucial: > > 1) $1.6 million on average is what one single spear phishing > attack costs for organizations > 2) $500 million every year is scammed by phishing attacks > 3) Just 3% of all users will report phishing emails to their > management > 4) More than 400 businesses are targeted by BEC scams every day > 5) 76% of organizations have reported that they have been victims > of a phishing attack. > 6) 1 in 3 companies have been victims of CEO fraud emails > 7) 70% of all global emails is malicious > 8) Fake invoice messages are the #1 type of phishing lure > > You can find the SPF fix over here : > > https://www.digitalocean.com/community/tutorials/how-to-use-an-spf-record-to-prevent-spoofing-improve-e-mail-reliability > < > https://www.digitalocean.com/community/tutorials/how-to-use-an-spf-record-to-prevent-spoofing-improve-e-mail-reliability > > > > > For DMARC record :https://easydmarc.com/blog/how-to-fix-no- > <https://easydmarc.com/blog/how-to-fix-no->dmarc-record-found/ > > and DMARC policy here: > https://support.rackspace.com/how-to/create-a- > <https://support.rackspace.com/how-to/create-a->dmarc-policy/ > > Let me know if you need me to send a forged email. > > *Note:*Eagerly awaiting your approval for the bounty reward tied to > my recent security contribution. Let's continue the journey > togetherand will be reporting other vulnerabilities accordingly. > > > Stay Safe & Healthy. > > Jed Rip > > *Snapshots:* > > image.png > image.png > > Passing along this weird email. > > > -------- Forwarded Message -------- > Subject: Re: Vulnerability Report: (Email Spoofing) > Resent-Date: Mon, 02 Dec 2024 08:14:03 +0000 > Resent-From: membership@w3.org > Date: Mon, 2 Dec 2024 13:11:36 +0500 > From: Jed Rip <jed.rip.protector@gmail.com> <jed.rip.protector@gmail.com> > To: membership@w3.org, invoicing@w3.org, w3t-pr@w3.org, > team-liaisons@w3.org, public-website-redesign@w3.org, sysreq@w3.org, > contact@w3.org > > Hello, > > How are you? > > I haven't received any update from you yet. > I am eagerly waiting for your reply. > Could you please confirm with me about the reported vulnerability and its > bounty reward? > > Looking forward to hearing from you soon. > > Thanks and Regards, > > On Sun, Oct 6, 2024 at 7:20 AM Jed Rip <jed.rip.protector@gmail.com> > wrote: > >> Hello Team, >> >> >> I am a security researcher and I provide information and knowledge >> regarding “Vulnerability" on websites. I have found some vulnerabilities on >> your website/domain. >> >> *DESCRIPTION:* >> >> >> I just sent a forged email to my email address that appears to originate >> from membership@w3.org I was able to do this because of the following: >> >> DMARC record lookup and validation for w3.org >> >> “No DMARC Record found” >> And/ OR >> "DMARC Quarantine/Reject policy not enabled" >> >> >> *Fix: *1) Publish DMARC Record. (If not already Published) >> 2)Enable DMARC Quarantine/Reject policy >> 3)Your DMARC record should look like >> "v=DMARC1; p=reject; sp=none; pct=100; ri=86400; rua=mailto: >> info@domain.com" >> >> *And* >> >> As I have seen the SPF and TXT record for the w3.org which is : >> >> >> Found v=spf1 record for w3.org: >> v=spf1 include:_spf.google.com ~all >> >> >> so valid record will look like : >> >> >> Found v=spf1 record for w3.org: >> >> v=spf1 include:_spf.google.com -all >> >> >> >> >> *What's the issue : * >> What’s the issue: as u can see in the article difference between softfail >> and hardfail you should be using fail as Hardfail as it doesn’t allow >> anyone to send spoofed emails from your domains, In current SPF record you >> should replace (?) or >> >> (~) with (-) at last before all , - is strict which prevents all spoofed >> emails except if you are sending >> >> You can validate by testing yourself over here: mxtoolbox.com >> >> This is useful in phishing, and this type of vulnerability is newsworthy >> ( >> http://bits.blogs.nytimes.com/2015/04/09/sendgrid-email-breach-was-used-to-attack-coinbase-a-bitcoin-exchange/ >> >> >> https://medium.com/@hotbit/official-statement-notices-of-counterfeit-email-listing-hotbit-io-d1d240005d35 >> >> This can be done using any php mailer tool like this , >> >> <?php >> $to = "VICTIM@example.com"; >> $subject = "Password Change"; >> $txt = "Change your password by visiting here - [VIRUS LINK HERE]l"; >> $headers = "From: membership@w3.org"; >> mail($to,$subject,$txt,$headers); >> ?> >> >> *IMPACT:* >> Due to this vulnerability, any hacker can send a forged email to your >> customers using your domain .Thus, getting sensitive information of your >> customers like login details, downloading a virus/malware etc. >> >> Also When an attacker sends an email to your customers asking them to >> change their password. The customer, after seeing the mail, might consider >> the mail as legit and falls for the trap. >> >> In doing this the attacker can take them to his website where certain >> JavaScript is executed which steals the customer's session id and password. >> >> The results can be more dangerous and impactful. >> >> A study shows why DMARC and SPF are crucial: >> >> 1) $1.6 million on average is what one single spear phishing attack >> costs for organizations >> 2) $500 million every year is scammed by phishing attacks >> 3) Just 3% of all users will report phishing emails to their management >> 4) More than 400 businesses are targeted by BEC scams every day >> 5) 76% of organizations have reported that they have been victims of a >> phishing attack. >> 6) 1 in 3 companies have been victims of CEO fraud emails >> 7) 70% of all global emails is malicious >> 8) Fake invoice messages are the #1 type of phishing lure >> >> You can find the SPF fix over here : >> https://www.digitalocean.com/community/tutorials/how-to-use-an-spf-record-to-prevent-spoofing-improve-e-mail-reliability >> >> >> For DMARC record : https://easydmarc.com/blog/how-to-fix-no- >> dmarc-record-found/ >> >> and DMARC policy here: https://support.rackspace.com/how-to/create-a- >> dmarc-policy/ >> >> Let me know if you need me to send a forged email. >> >> *Note:* Eagerly awaiting your approval for the bounty reward tied to my >> recent security contribution. Let's continue the journey together and >> will be reporting other vulnerabilities accordingly. >> >> >> Stay Safe & Healthy. >> >> Jed Rip >> >> *Snapshots:* >> [image: image.png] >> [image: image.png] >> >
Attachments
- image/png attachment: image.png
- image/png attachment: 02-image.png
Received on Wednesday, 4 December 2024 06:24:04 UTC