- From: Krishnamurthy Ganesh B <ganeshsurfs@gmail.com>
- Date: Fri, 31 Mar 2023 10:56:59 +0530
- To: Johann Hofmann <johannhof@google.com>
- Cc: public-privacycg@w3.org, Martin Thomson <mt@mozilla.com>, wilander@apple.com
- Message-ID: <CAMmT1pKQ75WG9uMhiESBmSY8HFrBXy9WLwcQaDWy2XBYrAcitw@mail.gmail.com>
Hello Johann, Greetings. I appreciate the genuine follow up here. I have nothing much on my views other than a need for ethics, risk mitigation/ safety with zero trust as per my discussion. We are all humans. God bless. Have a nice day ahead. Regards, Ganesh B On Wed, Mar 29, 2023 at 8:06 PM Johann Hofmann <johannhof@google.com> wrote: > Hi all, I wanted to give some visibility to this group around efforts > we're making to improve the security posture of cross-site cookie blocking, > in WebAppSec. We'd love to get your thoughts and questions either in the > group discussion or directly on the repository. > > Thanks! > > Johann > > ---------- Forwarded message --------- > From: Johann Hofmann <johannhof@google.com> > Date: Wed, Mar 29, 2023 at 4:27 PM > Subject: Standardizing Security Semantics of Cross-Site Cookies > To: WebAppSec WG <public-webappsec@w3.org> > Cc: Dylan Cutler <dylancutler@google.com>, Kaustubha Govind < > kaustubhag@google.com> > > > Hi everyone, > > Dylan, Kaustubha and I have been working on a new proposal to converge > browsers on semantics for blocking cross-site cookies > <https://github.com/DCtheTall/standardizing-cross-site-cookie-semantics/>, > in the interest of solving security challenges that arise when cross-site > cookies continue to be allowed by default in certain edge cases. > > As we've outlined in the document, all browsers perform cross-site cookie > blocking a bit differently, with the main difference being that Chrome > adheres to the "site for cookies > <https://datatracker.ietf.org/doc/html/draft-ietf-httpbis-rfc6265bis-11#section-5.2.1>" > when determining cross-site-ness for cookie blocking, whereas Firefox and > Safari compare the top-level site without considering the ancestor chain. > This particularly impacts the "ABA" case when a site A embeds another site > B, which then embeds A again. > > We would like to default the web platform to the more secure behavior > here, but recognize that we have to consider viable methods for developers > to opt into the less secure alternative. One such method could be the Storage > Access API <https://github.com/privacycg/storage-access>. > > There are a lot more details in the document, and we'd appreciate your > feedback. We aim to present this topic at the 04/19 call > <https://github.com/w3c/webappsec/issues/620> and hope to see you all > there! > > Johann >
Attachments
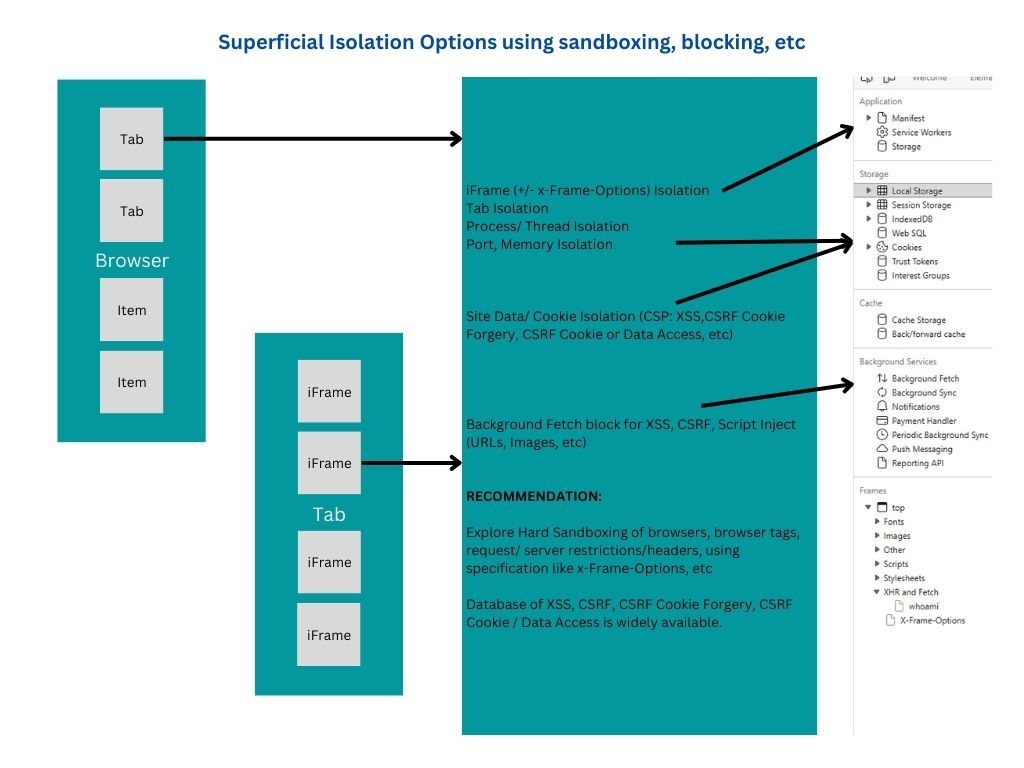
- image/jpeg attachment: Superficial_Layman_Non-Detailed_View__1_.jpg
- image/jpeg attachment: Web_capture_20-1-2023_174453_mail.google.com__1_.jpeg
- image/jpeg attachment: Sandboxing__Web_capture_22-6-2022_211742_twitter.com__1_.jpeg
Received on Friday, 31 March 2023 05:27:27 UTC