- From: Luis Barriga <luis.barriga@ericsson.com>
- Date: Thu, 11 Oct 2007 16:02:52 +0200
- To: "Web Security Context Working Group WG" <public-wsc-wg@w3.org>
- Message-ID: <1C6A13C92F510849B72272A71F9F3BCB01F1FC6B@esealmw105.eemea.ericsson.se>
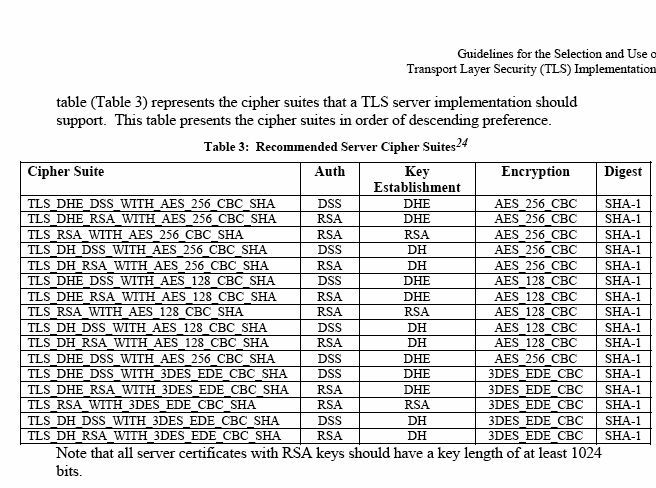
NIST has an online PDF document dated 2005: "Guidelines for the Selection and Use of Transport Layer Security (TLS) Implementations" http://csrc.nist.gov/publications/nistpubs/800-52/SP800-52.pdf At the end they have a table of recommended TLS server cypher suites that I took a snapshot and attach herewith. I think that we could consider the as "strong suites" (=combination of publi key + symmetric key + key lengths). One problem is that the selection criteria includes only FIPS-approved algorithms (a requirements for governmental use) which excludes RC4 and IDEA which can be cryptographically strong too. Luis -----Original Message----- From: public-wsc-wg-request@w3.org [mailto:public-wsc-wg-request@w3.org] On Behalf Of Web Security Context Working Group Issue Tracker Sent: den 11 oktober 2007 13:48 To: public-wsc-wg@w3.org Subject: ISSUE-128: Strong / weak algorithms? [Techniques] ISSUE-128: Strong / weak algorithms? [Techniques] http://www.w3.org/2006/WSC/track/issues/ Raised by: Thomas Roessler On product: Techniques The current text includes a placeholder for strong TLS alorithms, intended to be filled by reference. What do we put there? http://www.w3.org/2006/WSC/drafts/rec/rewrite.html#strong-algos
Attachments
- image/jpeg attachment: Recommended_TLS_Server_Cipher_Suites.jpg
Received on Thursday, 11 October 2007 14:03:20 UTC